Welcome to the second part in this series, this time we will setup on tag policy for your AWS resources, that will allow us to define efficient billing in next post, in order to proceed you need to have setup properly your AWS organization.
Tag Policy
An tag policy is a list of tag key (think project, company, private, …) with some more rules that can enforce: capitalization, restrict value to hardcoded content or regex, specific resources to enforce non-compliant one (this could have unintended effect so I would recommend to read this before using it).
So this step is another clickops operation, under AWS Organizations service you can activate different policies the one we want right now is "Tag policies".
Once this is done you need to create a new policies.
This new policy will be defined by it name, description and a list of "Tag Key".
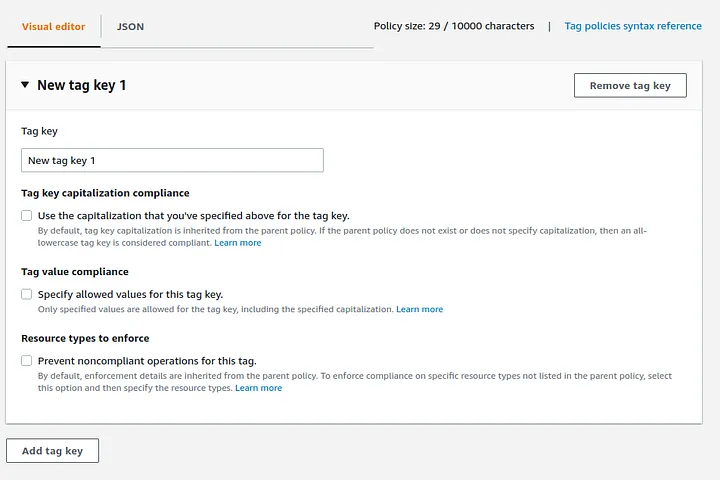
Also you can tag your tag policy if you want to feel meta.
After creating a tag policy you have to attach it on you account or root user.
This allow you to check which resources you created that are not compliant your tag using Tag Policies AWS service
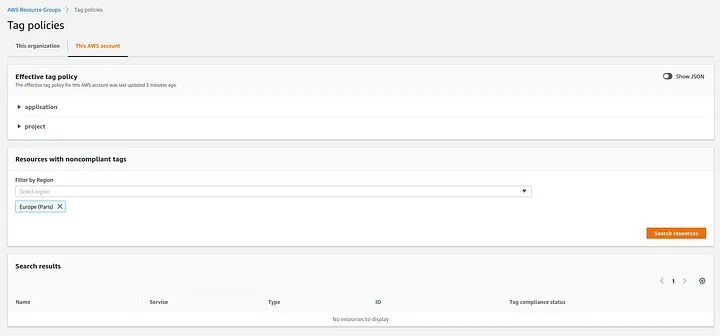
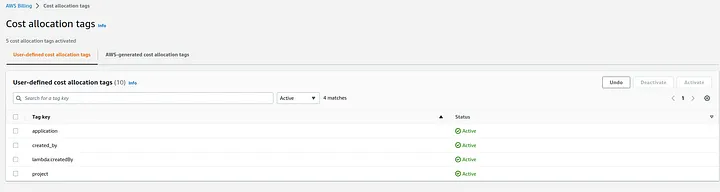
You can also start activating them in Billing as Cost allocation tags now that they are created and applied, it will matter in the next part of this series.
Terraform
Here the same configuration done using terraform (you still need to click on enable Tag policies in AWS Organization first)
resource "aws_organizations_policy" "global_default_billing" {
content = jsonencode(
{
tags = {
application = {
tag_key = {
"@@assign" = "application"
}
tag_value = {
"@@assign" = [
"frontend",
"backend",
"storage",
"database",
"crawler",
"api",
"billing"
]
}
}
project = {}
}
}
)
name = "global-default-billing"
tags = {"application": "billing"}
type = "TAG_POLICY"
}resource "aws_organizations_policy_attachment" "organization" {
policy_id = aws_organizations_policy.global_default_billing.id
target_id = "r-f8ph"
}resource "aws_ce_cost_allocation_tag" "application" {
tag_key = "application"
status = "Active"
}
resource "aws_ce_cost_allocation_tag" "project" {
tag_key = "project"
status = "Active"
}
We can go on step further by adding SCPs that can enforce at creation constraint like requiring tag on not allowing some role to change them but it can conflict with the way you allocate resource like cloudformation or SAM for example
Example SCPs for tagging resources
Hope you like it and stay tuned for the next parts in this series Clean AWS organization on your personal account part 3: budgets and billing reports