Hello here, this post will relate my journey to upgrade my own AWS account to "production like" standard in term of security, organization and billing, each article will try to have one clear goal.
This article will start first by explaining fundamental concepts
- ROOT user
- Organization
- AWS IAM Identity Center (previously AWS SSO)
- IAM roles
Then we show how to access your AWS account using tools like aws-sso-utils instead of default user.
Concepts
ROOT user
This will be your default user created by AWS when opening your account that will be the admin and have all the right official documentation.
Organization
This is the way AWS allow you to associates multiple account, setup global policy and a single point of billing official documentation.
AWS IAM Identity Center
Previously know as AWS SSO this is the way to create user and role that have SSO access, you can also have groups setup to avoid repeating setup for new user official documentation.
AWS roles
IAM roles regroup policy (what you can do with which services) that will be applied to a user or a group, those policies can be created by you or you can use the one already setup by AWS.
IAM roles
IAM roles are a new way to give temporary access, the result is almost the same from an user standpoint but the from the account administrator you have a IAM role were you allow people to log into official documentation.
Setting SSO access
One of the most fundamental concept in security The Principle of Least Privilege, states that a subject should be given only those privileges needed for it to complete its task, so as we saw before root user is able to do anything on your AWS account, so we need to setup other ways to access your AWS account in a more restricted way.
At the beginning people used to created user, give them roles and create credentials (AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY) to store in their computer but, the risk was to have this credential compromised and the switch between credential could mean you deployed on prod by accident.
The new recommended way for user is to create user on AWS IAM Identity Center that can have temporary credential generated using SSO.
Assuming you just created the root account, I would recommend setting Multi-factor authentication (MFA)
We now need to activate organization lucky for us this don’ t cost anything, and will unlock lot of services we will discuss in more detail later, one this advantage and the ability to aggregate more account under this single organization umbrella, that something you will want for production ready env (one account by env, department, team, …).
We can link federated user from other tools like Okta for example but we will keep it out of this article as this is too much for a personal account with only pet project.
You need to go to service AWS SSO and select your account user under root.
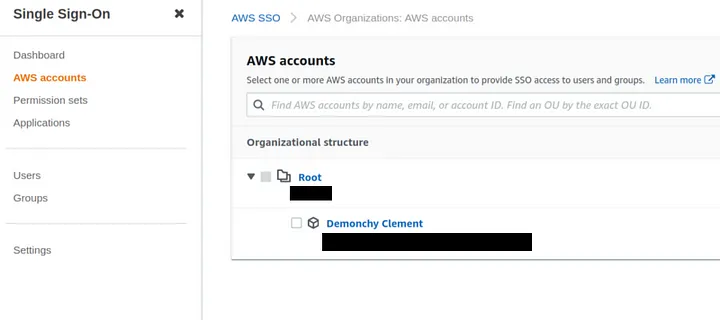
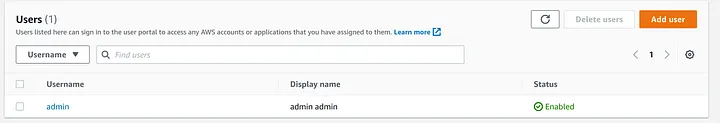
Here we will create an new admin user.
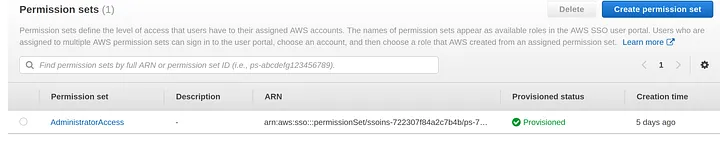
Then navigate under permission set to give it one that is already provided by AWS AdministratorAccess.
We now have to set an local profile that can use you new
[profile admin]
sso_start_url = <FETCH FROM YOUR AWS IAM IDENTITY CENTER CONSOLE>
sso_region = us-east-1
sso_account_id = <YOUR ACCOUNT ID>
sso_role_name = AdministratorAccess
region = us-east-1
output = json
I lost some time making this work because the sso_role_name didn't work with the role name but with the permission set name in this case.
aws sso login — profile admin; export AWS_PROFILE=admin
You can also use this great tools to this setup, specify your role with each command and even start AWS console directly aws-sso-utils
Next step would be to create new users with more appropriate permission set, like ML related account, read only access for customer and monitoring, etc …
If you want to go deep into the security parts I recommend you look at how to enforce it at the organization level with AWS SCPs and dig deeper into monitoring of the accounts AWS detective, AWS GuardDuty.
Hope you like it and stay tuned for the next parts in this series Clean AWS organization on your personal account part 2: enforce tag policy